Air gap environment preparation#
This topic provides guidance for preparing an air-gapped environment and installing an air-gapped environment system for a straightforward installation of Package Security Manager (On-prem), as detailed in Air gap installation.
Preparing the air-gapped environment#
Hardware requirements#
CPU - 4 cores
16GB RAM
- 1.5TB storage space
Conda_air gap zip file is ~1.1TB
CVE zip file is ~100MB
When partitioning space, allocate 20GB for /var/lib and the remaining 1.5TB for /opt/anaconda.
Software requirements#
The installer is a self-extracting binary that contains all the necessary components to run Package Security Manager services. The basic requirements prior to installation are:
Any Linux variant capable of supporting Docker
Use a fully qualified domain name (FQDN) or Hostname
DNS record and TLS/SSL certs
Make sure that SELinux is not in enforcing mode, either by disabling it or putting it in
permissivemode in the/etc/selinux/configfile. If it is in enforcing mode, you will need to reboot your instance after updating. After rebooting, run the following command to verify that SELinux is not being enforced:
# The result should be either Disabled or Permissive
getenforce
Docker Engine 23.x+ (Supports Compose format 3.8)
Docker Compose 2.1+ (Supports Compose format 3.8)
RHEL8+
Package Security Manager version 6.3.0+
Docker Compose 2.1+ (Supports Compose format 3.8)
Complete the Podman setup
Podman setup requires you to download and configure the podman-docker package. This package converts docker commands into their corresponding podman commands.
Note
You might need to work with your IT department to secure the
podman-dockerpackage.
Install the required software by running the following commands:
sudo yum install -y podman-docker sudo yum install netavark curl -SL https://github.com/docker/compose/releases/download/v2.23.0/docker-compose-linux-x86_64 -o /usr/local/bin/docker-compose
Using your preferred file editor, open the
usr/share/containers/containers.conffile and verify thenetwork_backend=value is set to"netavark". If it is not, set the value now, and save your changes.If necessary, make your
docker-composevolume executable by running the following command:sudo chmod +x /usr/local/bin/docker-compose
Create a symbolic link by running the following command:
sudo ln -s /usr/local/bin/docker-compose /usr/bin/docker-compose
Enable the
podman.socketby running the following commands:sudo systemctl enable --now podman.socket sudo systemctl status podman.socket
Verify that the podman socket works by running the following command:
sudo curl -w "\n" -H "Content-Type: application/json" --unix-socket /var/run/docker.sock http://localhost/_ping
Downloading packages and CVE files#
Downloading packages and CVEs#
In this section, you will download Package Security Manager packages and CVEs.
Note
Downloading Package Security Manager Packages may take several hours.
Choose a set of commands to download the Anaconda repository and cve packages:
All platforms
Run the following commands to download the Anaconda repository for all platforms:
curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_msys2.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/cve.zipRun the following commands to download the corresponding checksum files:
curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_msys2.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/cve.sha256Note
Downloading the
conda_msys2.zipandconda_r.zipfiles is optional.
Windows airgap files
Run the following commands to download the
mainrepository for Windows systems only:curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_win-32.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_win-64.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_noarch.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_msys2.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/cve.zipRun the following commands to download the corresponding checksum files:
curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_win-32.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_win-64.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_noarch.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_msys2.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/cve.sha256Run the following commands to download the
rrepository for Windows systems only:curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_win-32.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_win-64.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_noarch.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_msys2.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/cve.zipRun the following commands to download the corresponding checksum files:
curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_win-32.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_win-64.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_noarch.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_msys2.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/cve.sha256
Linux airgap files
Run the following commands to download the
mainrepository for Linux systems only:curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_linux-32.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_linux-64.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_linux-aarch64.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_linux-armv6l.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_linux-armv7l.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_linux-ppc64le.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_linux-s390x.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_noarch.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/cve.zipRun the following commands to download the corresponding checksum files:
curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_linux-32.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_linux-64.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_linux-aarch64.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_linux-armv6l.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_linux-armv7l.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_linux-ppc64le.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_linux-s390x.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_noarch.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/cve.sha256Run the following commands to download the
rrepository for Linux systems only:curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_linux-32.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_linux-64.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_linux-ppc64le.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_noarch.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/cve.zipRun the following commands to download the corresponding checksum files:
curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_linux-32.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_linux-64.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_linux-ppc64le.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_noarch.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/cve.sha256
MacOS airgap files
Run the following commands to download the
mainrepository for MacOS systems only:curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_osx-32.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_osx-64.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_osx-arm64.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_noarch.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/cve.zipRun the following commands to download the corresponding checksum files:
curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_osx-32.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_osx-64.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_osx-arm64.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_main_noarch.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/cve.sha256Run the following commands to download the
rrepository for MacOS systems only:curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_osx-64.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_noarch.zip curl -O https://anaconda-airgap-te.s3.amazonaws.com/cve.zipRun the following commands to download the corresponding checksum files:
curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_osx-64.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/conda_r_noarch.sha256 curl -O https://anaconda-airgap-te.s3.amazonaws.com/cve.sha256
Caution
Do not unzip the tarball files you’ve downloaded.
Validating Packages and CVEs#
To ensure that the files you’ve downloaded have not been tampered with, you must verify the integrity of the .zip files by running some commands to generate their SHA-256 cryptographic hashes (or “checksums”) and the cryptographic hashes for their corresponding .sha256 files, then checking the output to be sure they match. Choose a set of commands that corresponds with your setup:
File verification commands
If you downloaded your repository files on a Windows machine, run the following commands to view the hashes for the files:
# Replace <FILE> with a file that you downloaded Get-FileHash <FILE>.zip -Algorithm SHA256 Get-Content <FILE>.sha256If you downloaded your repository files on a Linux or MacOS machine, run the following commands to view the hashes for the files:
# Replace <FILE> with a file that you downloaded sha256sum <FILE>.zip cat <FILE>.sha256Note
You must run these commands for each for each file you downloaded.
DNS and TLS/SSL certificate requirements#
Package Security Manager can use certificates to provide transport layer security for the cluster. It is required to have your TLS/SSL certs prior to installation.
You may purchase certificates commercially, use Let’s Encrypt, or generate them using your organization’s internal public key infrastructure (PKI) system. When using an internal PKI-signed setup, the CA certificate is stored on the file system. You will need to make sure the root certificate of your certificate authority is trusted by the server running the application and the workstations used by users of the application.
DNS requirements
Web browsers use domain names and web origins to separate sites, so they cannot tamper with each other. If you want to use DNS, you must have it ready prior to installation. This DNS name is what users will use to access the application.
You must provide the SSL cert for the hostname your Package Security Manager instance is running on.
Security requirements#
External Ports#
These are ports that allow access outside of the server. It is important to protect all services running on the node from outside access. The exceptions are as shown below. These ports need to be open to allow access to Package Security Manager via browser and (optionally) via SSH:
:443nginx - only if you are using HTTPS:22ssh - optional; only if you need SSH
Internal Ports#
These are ports that allow access within the server and are open on docker containers, exposed only to the docker network. Ideally, Package Security Manager will have a dedicated environment. Package Security Manager uses several ports for internal communication between components. These ports do not need to be open to the end user but they need to be reserved, as some bind to the local host network interfaces.
You can run docker ps and reference the PORTS column, as shown in the following example:
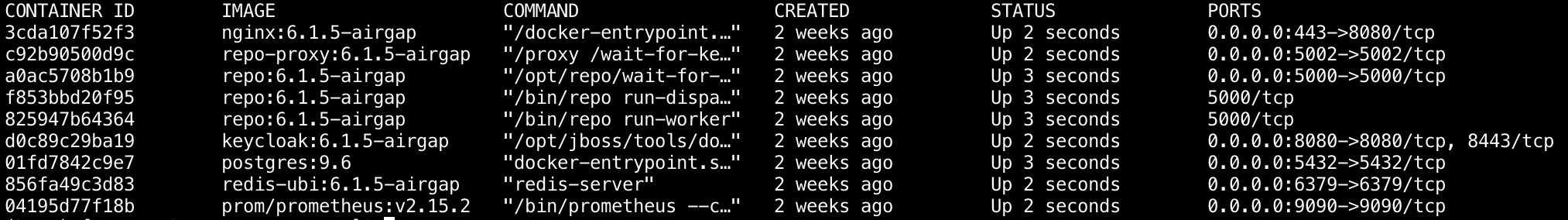
:5000repo - Package Security Manager API:5002repo-proxy - Package Security Manager file serving API proxy:5000repo-dispatcher - Package Security Manager event dispatcher/handler (exposed only for Prometheus metrics):5000repo-worker - Package Security Manager scheduled jobs worker (exposed only for Prometheus metrics):8080keycloak - Keycloak’s /auth/* endpoints are proxied in Nginx:5432postgres - Postgresql database used by Package Security Manager and Keycloak:6379redis - Redis instance used by Package Security Manager services:9090Prometheus - Prometheus is proxied in Nginx at /Prometheus
Enable IP address forwarding#
Forwarding IP addresses allows containers to communicate with one another on your host. You’ll need to configure these settings to allow non-root users to perform installations of Package Security Manager.
sysctl net.ipv4.conf.all.forwarding=1
sysctl net.ipv6.conf.all.forwarding=1
iptables -P FORWARD ACCEPT
System validation checks#
Once your environment is prepared, run the following commands to verify it is ready for installation of Package Security Manager.
System validation
To verify what type of processor your system is running and the number of CPUs present, run the command:
cat /proc/cpuinfo
To verify the amount of system memory is sufficient, run the command:
cat /proc/meminfo
To verify there is a sufficient amount of disk space for the installation, run the command:
df -h
To verify the kernel release version and processor type, run the command:
uname -a
To verify your operating system release version, run the command:
cat /etc/os-release
To verify your version of Docker, run the command:
docker version
To verify your version of docker-compose, run the command:
docker compose --version
After ensuring all requirements have been met, proceed to Air gap installation to install Package Security Manager in your air-gapped environment.