Viewing user login activity¶
You can directly query the Keycloak application programming interface (API) to view your Anaconda Server user login activity.
Prerequisites¶
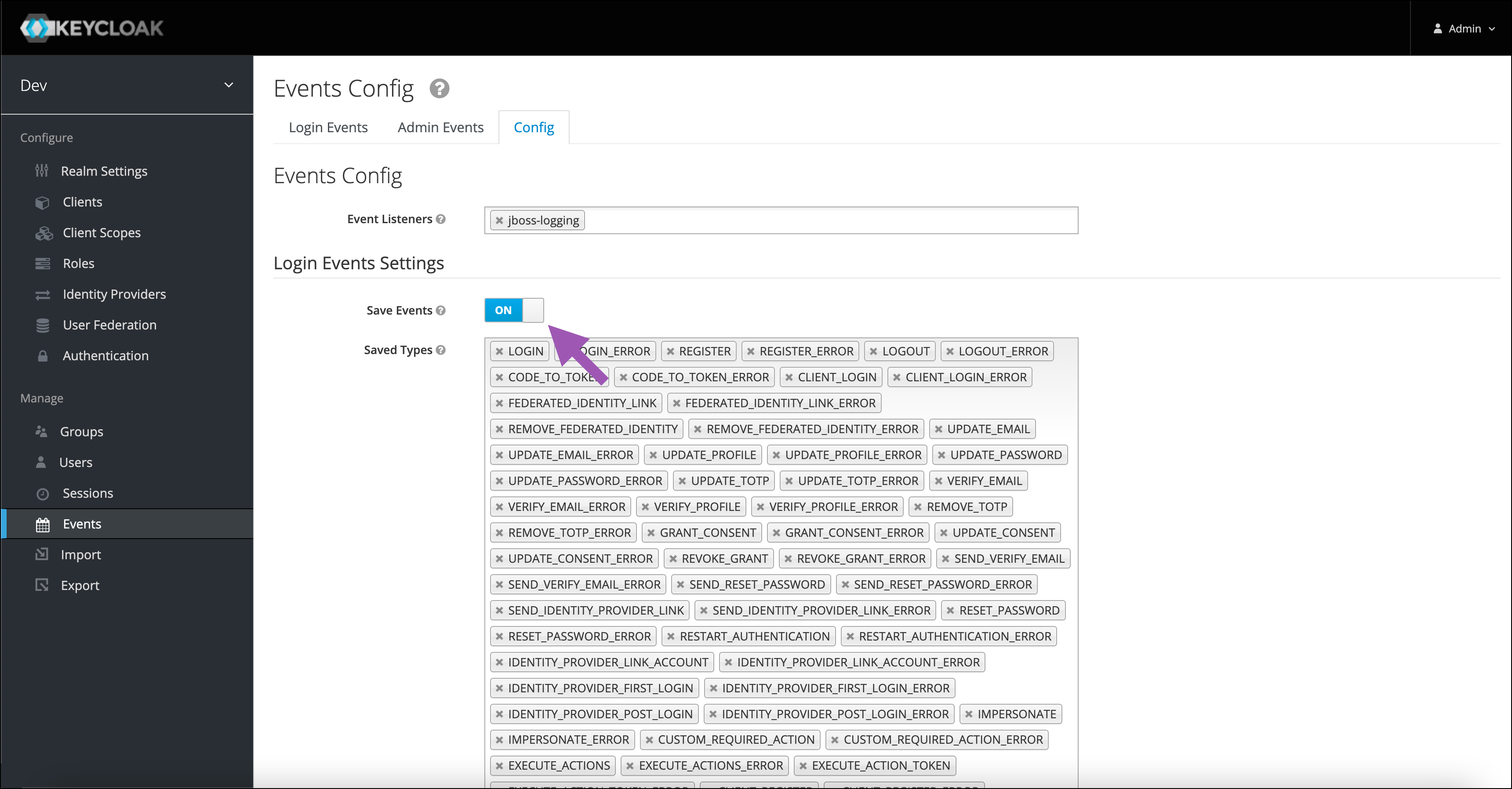
You must have Events enabled within Keycloak to track login events.
Select Events from the left-hand navigation, then open the Config tab.
Verify the Save Events toggle is set to
ON.
Querying the Keycloak API¶
Open a terminal. Generate a temporary token and store it as an enviornment variable for the Keycloak API by running the following command:
# Replace <URL> with your Anaconda Server URL # Replace <ADMIN> with your Keycloak admin user name # Replace <PASSWORD> with your Keycloak admin password export TKN=$(curl -X POST '<URL>/auth/realms/master/protocol/openid-connect/token' -H "Content-Type: application/x-www-form-urlencoded" --data-urlencode "username=<ADMIN>" --data-urlencode 'password=<PASSWORD>' --data-urlencode 'grant_type=password' --data-urlencode 'client_id=admin-cli' | jq -r '.access_token')
Note
You can verify that your command generated a token by running the command
echo $TKN.This temporary token expires after 60 seconds, and the next command needs to be entered before the token expires! Don’t worry though, you can always generate another temporary token, if necessary.
Query the Keycloak API for
LOGINevents by running the following command:# Replace <URL> with your Anaconda Server URL curl -X GET <URL>/auth/admin/realms/dev/events -H "accept: application/json" -H "Authorization: Bearer $TKN " -d "{\"type\":\"LOGIN\"}" | jq
Example¶
Let’s say your Anaconda Server URL is https://data_science_snakes.anaconda.com, and your Keycloak administrator’s username is admin and their password is password.
Once you’ve verified that Keycloak is saving user login events, request a temporary token from the Keycloak API with the following command:
export TKN=$(curl -X POST 'https://data_science_snakes.anaconda.com/auth/realms/master/protocol/openid-connect/token' -H "Content-Type: application/x-www-form-urlencoded" --data-urlencode "username=admin" --data-urlencode 'password=password' --data-urlencode 'grant_type=password' --data-urlencode 'client_id=admin-cli' | jq -r '.access_token')
Before the token expires, run the following command to query the Keycloak API for Anaconda Server user login events:
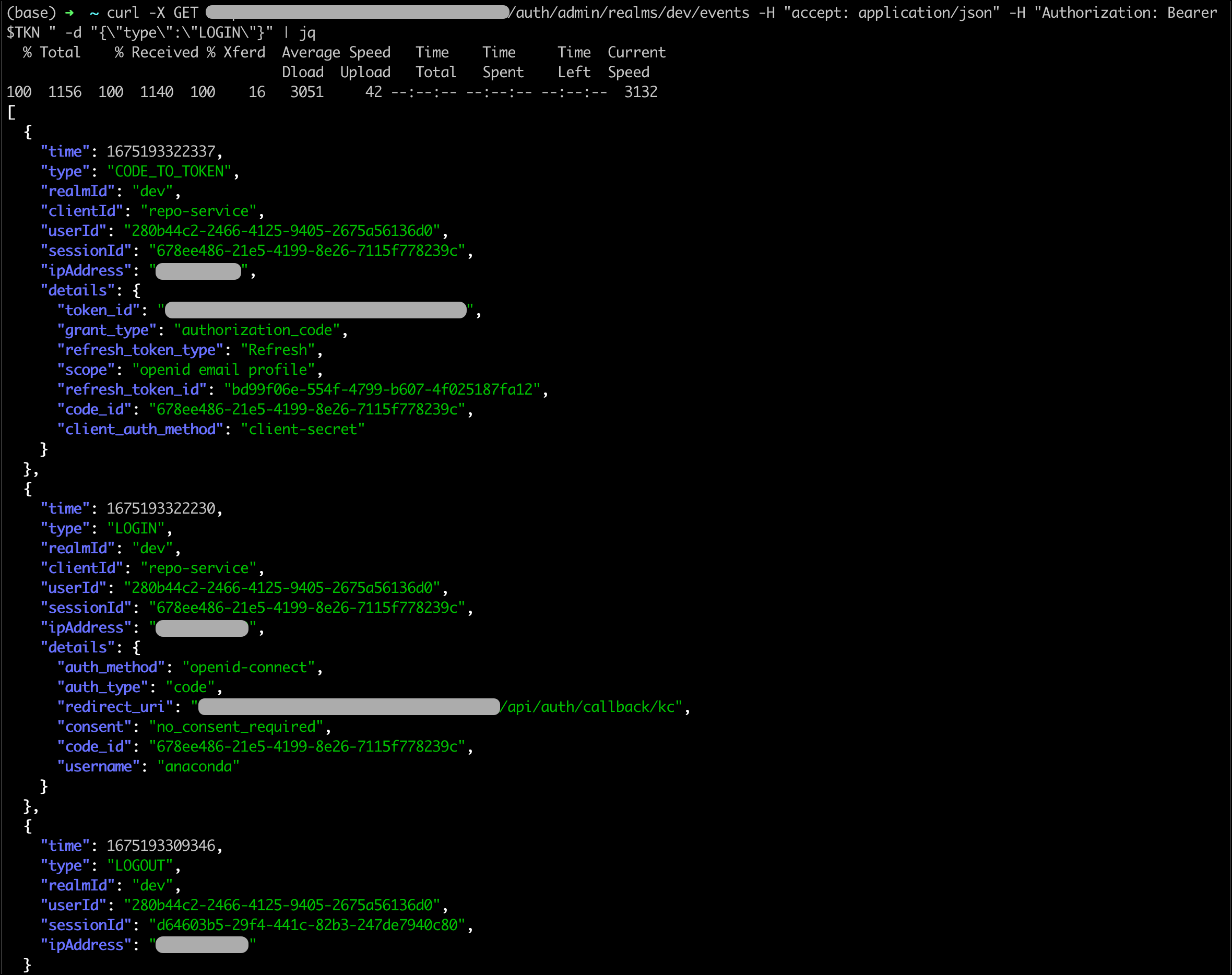
curl -X GET https://data_science_snakes.anaconda.com/auth/admin/realms/dev/events -H "accept: application/json" -H "Authorization: Bearer $TKN " -d "{\"type\":\"LOGIN\"}" | jq
If your query is processed correctly, your return will look something like this: